Hello!<br>
As you can see, this is not a formal email, and unfortunately, it does not mean anything good for you. <br>
BUT do not despair, it is not critical. I am going to explain to you everything right now. <br>
<br>
I have access to your electronic devices, which are the part of the local network you regularly use. <br>
I have been tracking your activity for the last few months. <br>
<br>
How did that happen?<br>
You visited some hacked websites with Exploit, and your device was exposed to my malicious software (I bought it in Darknet from specialists in this field).<br>
This is a very complex software, operating as Trojan Horse. It updates regularly, and your antivirus can not detect it. <br>
The program has a keylogger; it can turn your camera and microphone on and off, send files and provide access to your local network. <br>
<br>
It took me some time to get access to the information from other devices, and as of now, I have all your contacts with conversations, info about your locations, what you like, your favourite websites, etc. <br>
Honestly, I meant nothing bad at first and did that just for fun. This is my hobby. <br>
<br>
But I got HIV and unfortunately lost my job. <br>
And I figured out how to use "my hobby" to get money from you! <br>
I recorded a video of you masturbating. This video has a separated screen, where you can be easily recognised; also, it can be clearly seen what sort of video you prefer. <br>
Well, I am not proud of this, but I need money to survive. <br>
<br>
Let's make a deal. You pay me as much as I ask you to, and I won't send this video to your friends, family, and other acquaintances. <br>
You should understand, this is not a joke. I can send it by email, through SMS-link, social media, even post it in mass media (I have got some hacked accounts of their admins).<br>
So you can become Twitter or Instagram "Star"! <br>
<br>
To avoid this, you should send me 1,290 USD in Bitcoins on my BTC wallet:1PserZTMVttdiUno9SQi6gJjSyhAnFwP2Q<br>
<br>
If you don't know how to use Bitcoins, search it in Bing or Google <<how can I purchase Bitcoins>> or other stuff like that. <br>
I will delete the video as soon as I receive the money. I will also delete the malicious software from your device, and you will never hear from me again. <br>
I'll give you 2 days, that's more than enough, I think. Time tracking will start as soon as you open this email, I am monitoring this! <br>
<br>
And one last thing:<br>
It makes no sense to report about this to the police since I am using TOR, so there is no way to track Bitcoin transactions. <br>
Don't respond to me (I generated this letter in your account and put the real address of the man who has no idea about this). In such a way, I make it impossible to track me.<br>
<br>
If you ever do something stupid or against my expectations, I will immediately share this video. <br>
Good luck!<br>
quinta-feira, 26 de junho de 2025
sábado, 16 de novembro de 2024
There is an overdue payment under your name. Please, settle your debts ASAP.
Hi!
Sadly, there are some bad news that you are about to hear.
About few months ago I have gained a full access to all devices used by you for internet browsing.
Shortly after, I started recording all internet activities done by you.
Below is the sequence of events of how that happened:
Earlier I purchased from hackers a unique access to diversified email accounts (at the moment, it is really easy to do using internet).
As you can see, I managed to log in to your email account without breaking a sweat: (fatimamerigue.inspiracaoeacao@blogger.com).
Within one week afterwards, I installed a Trojan virus in your Operating Systems available on all devices that you utilize for logging in your email.
To be frank, it was somewhat a very easy task (since you were kind enough to open some of links provided in your inbox emails).
I know, you may be thinking now that I'm a genius.
With help of that useful software, I am now able to gain access to all the controllers located in your devices (e.g., video camera, keyboard, microphone and others).
As result, managed to download all your photos, personal data, history of web browsing and other info to my servers without any problems.
Moreover, I now have access to all accounts in your messengers, social networks, emails, contacts list, chat history - you name it.
My Trojan virus continues refreshing its signatures in a non-stop manner (because it is operated by driver),
hence it remains undetected by any antivirus software installed in your PC or device.
So, I guess now you finally understand the reason why I could never be caught until this very letter...
During the process of your personal info compilation, I could not help but notice that you are a huge admirer and regular guest of websites with adult content.
You endure a lot of pleasure while checking out porn websites, watching nasty porn movies and reaching breathtaking orgasms.
Let me be frank with you, it was really hard to resist from recording some of those naughty solo scenes with you in main role and compiling them in special videos
that expose your masturbation sessions, which end with you cumming.
In case if you still have doubts, all I need is to click my mouse and all those nasty videos with you will be shared to friends, colleagues, and relatives of yours.
Moreover, nothing stops me from uploading all that hot content online, so all public can watch it too.
I sincerely hope, you would really not prefer that to happen, keeping in mind all the dirty things you like to watch,
(you certainly know what I mean) it will completely ruin your reputation.
However, don't worry, there is still a way to resolve this:
You need to carry out a $1290 USD transfer to my wallet (equivalent amount in bitcoins depending on exchange rate at the moment of funds transfer),
hence upon receiving the transaction, I will proceed with deleting all the filthy videos with you in main role.
Afterwards, we can forget about this unpleasant accident. Furthermore, I guarantee that all the malicious software will also be erased from your devices and accounts.
Mark my words, I never lie.
That is a great bargain with a low price, I assure you, because I have spent a lot of effort while recording
and tracking down all your activities and dirty deeds during a long period of time.
In case if you have no idea how to buy and transfer bitcoins - feel free to check the related info on the internet.
Here is my bitcoin wallet for your reference: bc1qzxtljgynvlxuxrasadla0kpxfmvue24hyedltn
From now on, you have only 48 hours and countdown has started once you opened this very email (in other words, 2 days).
The following list contains things you should definitely abstain from doing or even attempting:
> Abstain from trying to reply this email (since the email is generated inside your inbox alongside with return address).
> Abstain from trying to call or report to police or any other security services. In addition, it's a bad idea if you want to share it with your friends,
hoping they would help. If I happen to find out (knowing my awesome skills, it can be done effortlessly,
because I have all your devices and accounts under my control and unceasing observation) - kinky videos of yours will be share to public the same day.
> Abstain from trying to look for me - that would not lead anywhere either. Cryptocurrency transactions are absolutely anonymous and cannot be tracked.
> Abstain from reinstalling your OS on devices or throwing them away. That would not solve the problem as well,
since all your personal videos are already uploaded and stored at remote servers.
Things you may be confused about:
> That your funds transfer won't be delivered to me.
Chill, I can track down any transactions right away, so upon funds transfer I will receive a notification as well,
since I still control your devices (my trojan virus has ability of controlling all processes remotely, just like TeamViewer).
> That I am going to share your dirty videos after receiving money transfer from you.
Here you need to trust me, because there is absolutely no point to still bother you after receiving money.
Moreover, if I really wanted all those videos would be available to public long time ago!
I believe we can still handle this situation on fair terms!
Here is my last advice to you... in future you better ensure you stay away from this kind of situations!
My advice - don't forget to regularly update your passwords to feel completely secure.
Sadly, there are some bad news that you are about to hear.
About few months ago I have gained a full access to all devices used by you for internet browsing.
Shortly after, I started recording all internet activities done by you.
Below is the sequence of events of how that happened:
Earlier I purchased from hackers a unique access to diversified email accounts (at the moment, it is really easy to do using internet).
As you can see, I managed to log in to your email account without breaking a sweat: (fatimamerigue.inspiracaoeacao@blogger.com).
Within one week afterwards, I installed a Trojan virus in your Operating Systems available on all devices that you utilize for logging in your email.
To be frank, it was somewhat a very easy task (since you were kind enough to open some of links provided in your inbox emails).
I know, you may be thinking now that I'm a genius.
With help of that useful software, I am now able to gain access to all the controllers located in your devices (e.g., video camera, keyboard, microphone and others).
As result, managed to download all your photos, personal data, history of web browsing and other info to my servers without any problems.
Moreover, I now have access to all accounts in your messengers, social networks, emails, contacts list, chat history - you name it.
My Trojan virus continues refreshing its signatures in a non-stop manner (because it is operated by driver),
hence it remains undetected by any antivirus software installed in your PC or device.
So, I guess now you finally understand the reason why I could never be caught until this very letter...
During the process of your personal info compilation, I could not help but notice that you are a huge admirer and regular guest of websites with adult content.
You endure a lot of pleasure while checking out porn websites, watching nasty porn movies and reaching breathtaking orgasms.
Let me be frank with you, it was really hard to resist from recording some of those naughty solo scenes with you in main role and compiling them in special videos
that expose your masturbation sessions, which end with you cumming.
In case if you still have doubts, all I need is to click my mouse and all those nasty videos with you will be shared to friends, colleagues, and relatives of yours.
Moreover, nothing stops me from uploading all that hot content online, so all public can watch it too.
I sincerely hope, you would really not prefer that to happen, keeping in mind all the dirty things you like to watch,
(you certainly know what I mean) it will completely ruin your reputation.
However, don't worry, there is still a way to resolve this:
You need to carry out a $1290 USD transfer to my wallet (equivalent amount in bitcoins depending on exchange rate at the moment of funds transfer),
hence upon receiving the transaction, I will proceed with deleting all the filthy videos with you in main role.
Afterwards, we can forget about this unpleasant accident. Furthermore, I guarantee that all the malicious software will also be erased from your devices and accounts.
Mark my words, I never lie.
That is a great bargain with a low price, I assure you, because I have spent a lot of effort while recording
and tracking down all your activities and dirty deeds during a long period of time.
In case if you have no idea how to buy and transfer bitcoins - feel free to check the related info on the internet.
Here is my bitcoin wallet for your reference: bc1qzxtljgynvlxuxrasadla0kpxfmvue24hyedltn
From now on, you have only 48 hours and countdown has started once you opened this very email (in other words, 2 days).
The following list contains things you should definitely abstain from doing or even attempting:
> Abstain from trying to reply this email (since the email is generated inside your inbox alongside with return address).
> Abstain from trying to call or report to police or any other security services. In addition, it's a bad idea if you want to share it with your friends,
hoping they would help. If I happen to find out (knowing my awesome skills, it can be done effortlessly,
because I have all your devices and accounts under my control and unceasing observation) - kinky videos of yours will be share to public the same day.
> Abstain from trying to look for me - that would not lead anywhere either. Cryptocurrency transactions are absolutely anonymous and cannot be tracked.
> Abstain from reinstalling your OS on devices or throwing them away. That would not solve the problem as well,
since all your personal videos are already uploaded and stored at remote servers.
Things you may be confused about:
> That your funds transfer won't be delivered to me.
Chill, I can track down any transactions right away, so upon funds transfer I will receive a notification as well,
since I still control your devices (my trojan virus has ability of controlling all processes remotely, just like TeamViewer).
> That I am going to share your dirty videos after receiving money transfer from you.
Here you need to trust me, because there is absolutely no point to still bother you after receiving money.
Moreover, if I really wanted all those videos would be available to public long time ago!
I believe we can still handle this situation on fair terms!
Here is my last advice to you... in future you better ensure you stay away from this kind of situations!
My advice - don't forget to regularly update your passwords to feel completely secure.
terça-feira, 13 de agosto de 2024
>>> Your account is hacked. Your data is stolen. Learn how to regain access.
> Hi,
>
> I am a hacker, and I have successfully gained access to your operating system.
> I also have full access to your account.
>
> I've been watching you for a few months now.
>
> The fact is that your computer has been infected with malware through an adult site that you visited.
> If you are not familiar with this, I will explain.
> Trojan Virus gives me full access and control over a computer or other device.
> This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.
> I also have access to all your contacts and all your correspondence.
>
> Why did your antivirus not detect malware?
> Answer: The malware I used is driver-based, I update its signatures every 4 hours. Hence your antivirus is unable to detect its presence.
> I made a video showing how you satisfy yourself in the left half of the screen, and the right half shows the video you were watching at the time.
>
> With one mouse click, I can send this video to all your emails and contacts on your social networks.
> I can also make public all your e-mail correspondence and chat history on the messengers that you use.
>
> If you don't want this to happen, transfer $880 in Bitcoin equivalent to my Bitcoin address (if you do not know how to do this, just search "buy bitcoin" on Google).
>
> My Bitcoin address (BTC Wallet) is: 1D9NgNsdmYXMYbw2z4oxEJvTwx1ut3F7o3
>
> After confirming your payment, I will delete the video immediately, and that's it. You will never hear from me again.
> I will give you 50 hours (more than 2 days) to pay. I will get a notice, when you open this email, and the timer will start.
> Filing a complaint somewhere does not make sense because this email cannot be tracked like my Bitcoin address.
>
> I never make any mistakes.
> If I find that you have shared this message with someone else, the video will be immediately distributed.
>
> Best regards!
>
> I am a hacker, and I have successfully gained access to your operating system.
> I also have full access to your account.
>
> I've been watching you for a few months now.
>
> The fact is that your computer has been infected with malware through an adult site that you visited.
> If you are not familiar with this, I will explain.
> Trojan Virus gives me full access and control over a computer or other device.
> This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.
> I also have access to all your contacts and all your correspondence.
>
> Why did your antivirus not detect malware?
> Answer: The malware I used is driver-based, I update its signatures every 4 hours. Hence your antivirus is unable to detect its presence.
> I made a video showing how you satisfy yourself in the left half of the screen, and the right half shows the video you were watching at the time.
>
> With one mouse click, I can send this video to all your emails and contacts on your social networks.
> I can also make public all your e-mail correspondence and chat history on the messengers that you use.
>
> If you don't want this to happen, transfer $880 in Bitcoin equivalent to my Bitcoin address (if you do not know how to do this, just search "buy bitcoin" on Google).
>
> My Bitcoin address (BTC Wallet) is: 1D9NgNsdmYXMYbw2z4oxEJvTwx1ut3F7o3
>
> After confirming your payment, I will delete the video immediately, and that's it. You will never hear from me again.
> I will give you 50 hours (more than 2 days) to pay. I will get a notice, when you open this email, and the timer will start.
> Filing a complaint somewhere does not make sense because this email cannot be tracked like my Bitcoin address.
>
> I never make any mistakes.
> If I find that you have shared this message with someone else, the video will be immediately distributed.
>
> Best regards!
quarta-feira, 17 de julho de 2024
I own very sensitive information about your web activities
Greetings!<br>
<br>
First of all, let me tell you, you are one of a kind!<br>
It is hard to impress me because I have seen a lot in my career as a professional hacker but now I am really impressed. <br>
<br>
I will get straight to the point. Listen to me carefully. <br>
<br>
Several months ago, <br>
I was able to hack your operating system and gain full access to all your devices and accounts including messengers, social media profiles, etc. <br>
<br>
I hope, now you begin to get my message. <br>
It goes without saying that I gained access to what you type via keylogger, your internet activity and webcam streaming. <br>
All of this was possible due to your frequent visits to adult websites infected with harmful malware. <br>
In other words, you were under my microscope for many days like some kind of a little bug.<br>
The only difference is that unlike you there is no bug in the world who like to watch pervert porn. <br>
<br>
Yes, you understand it right: I was able to see everything on your screen and record video and audio streams of your camera and microphone. <br>
All of these records are currently securely saved on my storage as well as a backup copy. <br>
<br>
In addition, I also gained access to your confidential information contained in your emails and chat messages.<br>
<br>
Probably you are wondering why your antivirus and spyware defender software allowed me to do all of this? <br>
I am sorry but it's a very stupid question. All antivirus programs turned into useless shit quite a long time ago. <br>
Have you ever heard last years about any "advanced" new technologies in this industry? <br>
Exactly. Nowadays, developers do not give a flying fuck about your security. Therefore, hackers like me took advantage of it. <br>
<br>
The more you know my friend, no need to thank me. <br>
Maybe with this fresh knowledge, you will be more serious about your internet security and never take it for granted anymore. <br>
<br>
With that out of the way, let's cut to the chase. Using your recordings I made a video compilation, <br>
which shows on the left side the controversial porn scenes of you happily masturbating to, <br>
while on the right side it demonstrates the video you were watching at that moment.. ^.^<br>
<br>
There are only 48 hours left since the moment you receive this email until I send this video to all your email and messenger contacts. <br>
But there is more, guess what? I can also make public all your emails and chat history.<br>
<br>
You are sick fuck in love with freaky adult content but you are not mentally retarted so I would like to believe, you do not want to let this happen. <br>
Right? Only the most stupid man in the world would be happy if his friends, loved ones and colleagues suddenly knew about something like this. <br>
<br>
In other words, there is no way back. It cannot be fixed. However, there is a way forward that both of us can benefit from. <br>
I am a reasonable guy and have no intention to ruin your life for nothing. I'd better like to gain something instead. <br>
<br>
Here is your salvation - transfer the Bitcoin equivalent of 790 USD to my Bitcoin account<br>
(you can google the process in case you don't know how to do that).<br>
<br>
Here is my Bitcoin address: 1854QQaFFbozEXBK16peLPvUW1JBdoQoCz<br>
<br>
Once I am notified of receiving it, I will delete all those videos and disappear from your life for good.<br>
As I mentioned, you have only 48 hours to make a transaction after you open this email.<br>
<br>
Believe me, I am always one step ahead so no way in hell you could fool me. <br>
If I discover that you shared this message with others, I will send and publish your videos in no time.<br>
<br>
P.S. It's in your power to make it nice for both of us.
<br>
First of all, let me tell you, you are one of a kind!<br>
It is hard to impress me because I have seen a lot in my career as a professional hacker but now I am really impressed. <br>
<br>
I will get straight to the point. Listen to me carefully. <br>
<br>
Several months ago, <br>
I was able to hack your operating system and gain full access to all your devices and accounts including messengers, social media profiles, etc. <br>
<br>
I hope, now you begin to get my message. <br>
It goes without saying that I gained access to what you type via keylogger, your internet activity and webcam streaming. <br>
All of this was possible due to your frequent visits to adult websites infected with harmful malware. <br>
In other words, you were under my microscope for many days like some kind of a little bug.<br>
The only difference is that unlike you there is no bug in the world who like to watch pervert porn. <br>
<br>
Yes, you understand it right: I was able to see everything on your screen and record video and audio streams of your camera and microphone. <br>
All of these records are currently securely saved on my storage as well as a backup copy. <br>
<br>
In addition, I also gained access to your confidential information contained in your emails and chat messages.<br>
<br>
Probably you are wondering why your antivirus and spyware defender software allowed me to do all of this? <br>
I am sorry but it's a very stupid question. All antivirus programs turned into useless shit quite a long time ago. <br>
Have you ever heard last years about any "advanced" new technologies in this industry? <br>
Exactly. Nowadays, developers do not give a flying fuck about your security. Therefore, hackers like me took advantage of it. <br>
<br>
The more you know my friend, no need to thank me. <br>
Maybe with this fresh knowledge, you will be more serious about your internet security and never take it for granted anymore. <br>
<br>
With that out of the way, let's cut to the chase. Using your recordings I made a video compilation, <br>
which shows on the left side the controversial porn scenes of you happily masturbating to, <br>
while on the right side it demonstrates the video you were watching at that moment.. ^.^<br>
<br>
There are only 48 hours left since the moment you receive this email until I send this video to all your email and messenger contacts. <br>
But there is more, guess what? I can also make public all your emails and chat history.<br>
<br>
You are sick fuck in love with freaky adult content but you are not mentally retarted so I would like to believe, you do not want to let this happen. <br>
Right? Only the most stupid man in the world would be happy if his friends, loved ones and colleagues suddenly knew about something like this. <br>
<br>
In other words, there is no way back. It cannot be fixed. However, there is a way forward that both of us can benefit from. <br>
I am a reasonable guy and have no intention to ruin your life for nothing. I'd better like to gain something instead. <br>
<br>
Here is your salvation - transfer the Bitcoin equivalent of 790 USD to my Bitcoin account<br>
(you can google the process in case you don't know how to do that).<br>
<br>
Here is my Bitcoin address: 1854QQaFFbozEXBK16peLPvUW1JBdoQoCz<br>
<br>
Once I am notified of receiving it, I will delete all those videos and disappear from your life for good.<br>
As I mentioned, you have only 48 hours to make a transaction after you open this email.<br>
<br>
Believe me, I am always one step ahead so no way in hell you could fool me. <br>
If I discover that you shared this message with others, I will send and publish your videos in no time.<br>
<br>
P.S. It's in your power to make it nice for both of us.
sexta-feira, 5 de abril de 2024
For your own safety, I highly recommend reading this email.
Hello,
You are in big trouble.
However, don't panic right away. Listen to me first, because there is always a way out.
You are now on the radar of an international group of hackers, and such things never end well for anyone.
I'm sure you've heard of Anonymous. Well, compared to us, they are a bunch of schoolboys.
We are a worldwide network of several thousand professionals, each with their own role.
Someone hacks corporate and government networks, someone cooperates with intelligence agencies on the most delicate tasks,
and someone (including me) deals with people like you to maintain the infrastructure of our group.
"What kind of people like me?" - that is the question you are probably asking yourself now.
The answer is simple: people who like to watch highly controversial and, shall we say,
unconventional pornography on the internet that most normal people would consider perverted.
But not you!
In order to leave you without any doubts, I'll explain how I found it out.
Two months ago, my colleagues and I installed spyware software on your computer and then gained access to all of your devices, including your phone.
It was easy - one of those many pop-ups on porn sites was our work.
I think you already understand that we would not write to an ordinary man who watches "vanilla" and even hardcore porn - there is nothing special about that.
But the things you're watching are beyond good and evil.
So after accessing your phone and computer cameras, we recorded you masturbating to extremely controversial videos.
There is a close-up footage of you and a little square on the right with the videos you're pleasing yourself.
However, as I said earlier, there is always a way out, because even the most degraded sinner deserves leniency.
You are lucky today because I am not a sadist who enjoys other people's suffering.
Only money matters to me.
Here is your salvation: you must transfer $1290 in Bitcoin to this BTC cryptocurrency wallet: 17XansAD9geWqX31sP7a8A3DmoVseVikyt
You have exactly 48 hours to make the payment, so think less, and do more.
As soon as I receive confirmation of the transaction, I will delete all compromising content and permanently disable our computer worm.
Believe me, I always abide by gentleman's agreements. Even with people who are hardly gentlemen. Because it's nothing personal, just business.
If I do not receive a payment, I will send all videos of you to every person in your contact list, messengers and email.
Relatives, loved ones, colleagues, friends-everyone you've ever been in contact with will receive them.
You understand perfectly well that you will never be able to wash this stain on your reputation.
Everyone will remember you as sick as fuck.
Your life will be completely ruined, and, most likely, only a tightened noose around your neck will be able to save the day.
If you haven't dealt with crypto before, I suppose it won't be difficult for you to figure it all out.
Simply type in the "crypto exchange" into the search bar and pay with a credit card. Besides, based on your browser history, you are a savvy user.
When you want to, you can dig into the darkest depths of the Internet, so I'm sure you will be able to find out what is what.
Here is what my colleagues and I should warn you against:
...Do not reply to this email. Do you really think we are so stupid to be tracked by an email address? This is a temporary disposable email.
As soon as I clicked "Send", it was gone for good.
...Forget about law-enforcement authorities. As soon as I see that you are trying to contact them, the compromising material will be published.
Remember, I have access to all your devices, and I can even track your movements.
...Do not reset your devices to factory settings and do not try to get rid of your devices.
It won't help in any way. Look above - my All-seeing eye is watching all your actions. It is easy to hunt you down.
I am sorry that we met in such circumstances. Probably, everything could be different if you had been more careful about what you are doing on the Internet.
Watch yourself from now on, because even such things that you previously considered insignificant can destroy your life in the future like a butterfly effect.
I hope this is goodbye forever. However, it depends on you.
P.S. The countdown is on. The choice is yours.
You are in big trouble.
However, don't panic right away. Listen to me first, because there is always a way out.
You are now on the radar of an international group of hackers, and such things never end well for anyone.
I'm sure you've heard of Anonymous. Well, compared to us, they are a bunch of schoolboys.
We are a worldwide network of several thousand professionals, each with their own role.
Someone hacks corporate and government networks, someone cooperates with intelligence agencies on the most delicate tasks,
and someone (including me) deals with people like you to maintain the infrastructure of our group.
"What kind of people like me?" - that is the question you are probably asking yourself now.
The answer is simple: people who like to watch highly controversial and, shall we say,
unconventional pornography on the internet that most normal people would consider perverted.
But not you!
In order to leave you without any doubts, I'll explain how I found it out.
Two months ago, my colleagues and I installed spyware software on your computer and then gained access to all of your devices, including your phone.
It was easy - one of those many pop-ups on porn sites was our work.
I think you already understand that we would not write to an ordinary man who watches "vanilla" and even hardcore porn - there is nothing special about that.
But the things you're watching are beyond good and evil.
So after accessing your phone and computer cameras, we recorded you masturbating to extremely controversial videos.
There is a close-up footage of you and a little square on the right with the videos you're pleasing yourself.
However, as I said earlier, there is always a way out, because even the most degraded sinner deserves leniency.
You are lucky today because I am not a sadist who enjoys other people's suffering.
Only money matters to me.
Here is your salvation: you must transfer $1290 in Bitcoin to this BTC cryptocurrency wallet: 17XansAD9geWqX31sP7a8A3DmoVseVikyt
You have exactly 48 hours to make the payment, so think less, and do more.
As soon as I receive confirmation of the transaction, I will delete all compromising content and permanently disable our computer worm.
Believe me, I always abide by gentleman's agreements. Even with people who are hardly gentlemen. Because it's nothing personal, just business.
If I do not receive a payment, I will send all videos of you to every person in your contact list, messengers and email.
Relatives, loved ones, colleagues, friends-everyone you've ever been in contact with will receive them.
You understand perfectly well that you will never be able to wash this stain on your reputation.
Everyone will remember you as sick as fuck.
Your life will be completely ruined, and, most likely, only a tightened noose around your neck will be able to save the day.
If you haven't dealt with crypto before, I suppose it won't be difficult for you to figure it all out.
Simply type in the "crypto exchange" into the search bar and pay with a credit card. Besides, based on your browser history, you are a savvy user.
When you want to, you can dig into the darkest depths of the Internet, so I'm sure you will be able to find out what is what.
Here is what my colleagues and I should warn you against:
...Do not reply to this email. Do you really think we are so stupid to be tracked by an email address? This is a temporary disposable email.
As soon as I clicked "Send", it was gone for good.
...Forget about law-enforcement authorities. As soon as I see that you are trying to contact them, the compromising material will be published.
Remember, I have access to all your devices, and I can even track your movements.
...Do not reset your devices to factory settings and do not try to get rid of your devices.
It won't help in any way. Look above - my All-seeing eye is watching all your actions. It is easy to hunt you down.
I am sorry that we met in such circumstances. Probably, everything could be different if you had been more careful about what you are doing on the Internet.
Watch yourself from now on, because even such things that you previously considered insignificant can destroy your life in the future like a butterfly effect.
I hope this is goodbye forever. However, it depends on you.
P.S. The countdown is on. The choice is yours.
domingo, 28 de janeiro de 2024
LEGALITY OF ETHICAL HACKING
Why ethical hacking?
Legality of Ehical Hacking

Ethical hacking is legal if the hacker abides by the rules stipulated in above section on the definition of ethical hacking.
Ethical hacking is not legal for black hat hackers.They gain unauthorized access over a computer system or networks for money extortion.

Legality of Ehical Hacking

Ethical hacking is legal if the hacker abides by the rules stipulated in above section on the definition of ethical hacking.
Ethical hacking is not legal for black hat hackers.They gain unauthorized access over a computer system or networks for money extortion.
Related posts
- Pentest Tools For Ubuntu
- Hacking Tools Kit
- Pentest Tools Android
- Hack Tool Apk No Root
- Hacking Tools 2019
- Pentest Tools Framework
- Hacking Tools And Software
- Hak5 Tools
- Hacker Tools Software
- Hacking Tools Free Download
- Android Hack Tools Github
- Hack Tools Download
- Hack Tools Download
- Hack Tools For Ubuntu
- World No 1 Hacker Software
- Hack Tools For Windows
- Free Pentest Tools For Windows
- Pentest Tools List
- Hacker Tools For Ios
- Black Hat Hacker Tools
- Pentest Tools Find Subdomains
- Hack Tools For Windows
- Top Pentest Tools
- Hacking Tools Free Download
- Pentest Tools List
- New Hack Tools
- How To Make Hacking Tools
- Android Hack Tools Github
- Bluetooth Hacking Tools Kali
- Free Pentest Tools For Windows
- Best Hacking Tools 2019
- Hacker Tool Kit
- Hacker Tools For Ios
- Termux Hacking Tools 2019
- Hacking Tools For Kali Linux
- Hack And Tools
- Hacking Tools For Kali Linux
- Hacking Tools For Windows 7
- Pentest Automation Tools
- Hacking Tools 2020
- Hacking Tools Kit
- Hack Tools For Games
- Hacking Tools For Pc
- Hacker Tools 2019
- Pentest Tools For Android
- Hacker Tools Free
- Blackhat Hacker Tools
- Hacking Tools And Software
- Hack Tools Mac
- How To Hack
- Hacker Tools Online
- Hack Tools For Mac
- Hacker Tools
- Hack Website Online Tool
- Hacker Tools Apk Download
- Hacking Tools 2019
- Hacking Tools 2020
- Hacking Tools For Windows Free Download
- Hack And Tools
- Ethical Hacker Tools
- Hacker Search Tools
- Hack Tools For Pc
- Hacking Tools Free Download
- Pentest Tools Github
- Hack And Tools
- Hacker Tools
- Hack Tools For Pc
- Hack Tools For Windows
- Pentest Tools For Windows
- Hacking Apps
- Computer Hacker
- Hack Tools Download
- Hack Rom Tools
- Hacker Hardware Tools
- Hacker Tools For Ios
- Pentest Tools Website
- Pentest Automation Tools
- Pentest Tools Review
- Pentest Tools Open Source
- Hacks And Tools
- Hack Tools 2019
- Hacking App
- Pentest Tools Github
- Tools For Hacker
- Github Hacking Tools
- Hacking Tools For Games
- Pentest Tools Online
- Hacker Tools Software
- Hacker Tools Apk Download
- Hack Rom Tools
- Pentest Recon Tools
- Hacker Techniques Tools And Incident Handling
- Hacking Tools For Windows Free Download
- Hack Tool Apk No Root
- Hacker
- Nsa Hack Tools Download
- Pentest Tools For Android
- Pentest Tools Open Source
- Hacking Tools 2020
- Pentest Tools Windows
- Best Pentesting Tools 2018
- Hacker Search Tools
- Physical Pentest Tools
- Hacker Techniques Tools And Incident Handling
- Hack Tools 2019
- Hacker Tools For Mac
- Pentest Box Tools Download
- Hack Tools
- Pentest Tools Android
- Hacking Tools 2020
- Hacker Tools List
- Hack Tools For Ubuntu
- Hacking Tools For Windows Free Download
- Tools For Hacker
- Pentest Tools List
- New Hack Tools
- Pentest Tools List
- Pentest Tools For Windows
- Pentest Tools List
- Hacking Tools Github
- Hacking Tools Hardware
- Tools Used For Hacking
- Hacker Tools Windows
- Hacking Tools
- Pentest Tools Framework
- Hack Tools 2019
- Pentest Tools Android
- Android Hack Tools Github
- Hak5 Tools
- Black Hat Hacker Tools
- World No 1 Hacker Software
- Underground Hacker Sites
- Hacking Tools Windows
- Hacking Tools For Windows 7
- Hack Tools Github
- Pentest Tools For Windows
- Pentest Tools Subdomain
- Hacking Tools For Kali Linux
- Pentest Tools Subdomain
- Hack Tools Download
- Hacker Tools Apk Download
- Hacker Tools Github
- How To Hack
- Pentest Tools Find Subdomains
- Hacking Tools Usb
- Hack Tools Pc
- Blackhat Hacker Tools
- Usb Pentest Tools
- Hack And Tools
WiFiJammer: Amazing Wi-Fi Tool
The name sounds exciting but really does it jam WiFi networks? Yes, it is able to do the thing which it's name suggests. So today I'm going to show you how to annoy your friend by cutting him/her short of the WiFi service.
Requirements:
- A computer/laptop with WiFi capable of monitoring (monitor mode).
- A Linux OS (I'm using Arch Linux with BlackArch Repos)
- And the most obvious thing wifijammer (If you're having BlackArch then you already have it).
How does it work? You maybe thinking!, it's quite simple it sends the deauth packets from the client to the AP (Access Point) after spoofing its (client's) mac-address which makes AP think that it's the connected client who wants to disconnect and Voila!
Well to jam all WiFi networks in your range its quite easy just type:
sudo wifijammer
but wait a minute this may not be a good idea. You may jam all the networks around you, is it really what you want to do? I don't think so and I guess it's illegal.
We just want to play a prank on our friend isn't it? So we want to attack just his/her AP. To do that just type:
sudo wifijammer -a <<AP-MAC-ADDRESS>>
here -a flag specifies that we want to jam a particular AP and after it we must provide the MAC-ADDRESS of that particular AP that we want to jam.
Now how in the world am I going to know what is the MAC-ADDRESS of my friend's AP without disturbing the other people around me?
It's easy just use the Hackers all time favorite tool airodump-ng. Type in the following commands:
sudo airmon-ng
sudo airodump-ng
airmon-ng will put your device in monitor mode and airodump-ng will list all the wifi networks around you with their BSSID, MAC-ADDRESS, and CHANNELS. Now look for your friend's BSSID and grab his/her MAC-ADDRESS and plug that in the above mentioned command. Wooohooo! now you are jamming just your friend's wifi network.
Maybe that's not what you want, maybe you want to jam all the people on a particular channel well wifijammer can help you even with that just type:
sudo wifijammer -c <<CHANNEL-NUMBER>>
with -c we specify to wifijammer that we only want to deauth clients on a specified channel. Again you can see with airodump-ng who is on which channel.
wifijammer has got many other flags you can check out all flags using this command that you always knew:
sudo wifijammer -h
Hope you enjoyed it, good bye and have fun :)
More info
- Growth Hacker Tools
- Hack Tools Pc
- Hacking Tools For Pc
- Pentest Tools Apk
- World No 1 Hacker Software
- Hacker
- World No 1 Hacker Software
- Hacking Tools Kit
- Hacker Tools Linux
- Hack Tools Github
- Pentest Tools Free
- World No 1 Hacker Software
- Hack Tools
- Pentest Tools Windows
- Hacker
- Usb Pentest Tools
- Pentest Tools Bluekeep
- Pentest Tools Nmap
- Hacking Tools Github
- Hacker Tools Mac
- Free Pentest Tools For Windows
- Physical Pentest Tools
- Hack Tools Mac
- Hacking Tools Pc
- Hack And Tools
- Hack Tool Apk
- Hack Tools
- Hack Tools For Ubuntu
- Pentest Tools Url Fuzzer
- Hacking Tools Software
- Free Pentest Tools For Windows
- Ethical Hacker Tools
- Hacking Tools For Mac
- Pentest Tools Subdomain
- Pentest Tools
- Tools 4 Hack
- Hacker Tools Online
- Hacking App
- Pentest Tools For Windows
- Hack Tools For Windows
- Hacking Tools Name
- Pentest Recon Tools
- Hack Tool Apk
- Hacker Tools Free
- Nsa Hack Tools
- Hacker Tools Mac
- Hak5 Tools
- Hackers Toolbox
- Wifi Hacker Tools For Windows
- Hacking Tools Hardware
- Pentest Tools Download
- Hacking Tools Windows
- Hack Tools 2019
- Hacking Tools Hardware
- Pentest Tools Tcp Port Scanner
- Pentest Tools For Ubuntu
- Android Hack Tools Github
- Pentest Tools Port Scanner
- Hacking Apps
- Hack Apps
- Hacking Tools Windows
- Hacking Tools For Mac
- Pentest Tools For Mac
- Hacker Tools 2019
- Blackhat Hacker Tools
- Hacker Tools Apk
- Install Pentest Tools Ubuntu
- Tools 4 Hack
- Hacking Tools
- Growth Hacker Tools
- Hack Website Online Tool
- Hacking Tools For Games
- How To Make Hacking Tools
- Hacking Tools For Beginners
- Pentest Tools Kali Linux
- Pentest Tools Website Vulnerability
- Hack Tools For Mac
- Hacking Tools Usb
- Hacker Hardware Tools
- Hacking Tools For Beginners
- Hacking Tools Hardware
- Hacker Search Tools
- Hack Website Online Tool
- Hacker Tools For Windows
- Pentest Tools Tcp Port Scanner
- Hacking Tools
- Pentest Box Tools Download
- Pentest Tools Windows
- Black Hat Hacker Tools
- Hacking Tools For Windows 7
- Hacker Search Tools
- Pentest Tools Website Vulnerability
- Hacker Tools Apk Download
- Hack Tools For Games
- Pentest Recon Tools
- Hacking Tools For Windows
- Hacker Tools Apk Download
- Install Pentest Tools Ubuntu
- Install Pentest Tools Ubuntu
- Hacker Tools Apk Download
- Pentest Tools Website
- Pentest Tools Download
- Pentest Tools Website
- Ethical Hacker Tools
- Hacking Tools And Software
- Hack Tools For Ubuntu
- Hacker Tools Online
- Android Hack Tools Github
- Tools 4 Hack
- Pentest Tools For Android
- Pentest Tools Find Subdomains
- How To Hack
- Hack Tools
- Pentest Tools Website Vulnerability
- Nsa Hack Tools
- Hacking Tools Kit
- Hacker Tools For Mac
- Pentest Tools Online
- Pentest Tools
- Hack Tools Online
- Pentest Tools Review
- What Is Hacking Tools
- Pentest Tools Download
- Hacker Tools For Pc
- Hacking Tools Software
- Hacking Tools Kit
- Nsa Hack Tools
- Pentest Recon Tools
- Hacking Tools For Pc
- Pentest Tools For Ubuntu
- Pentest Tools Online
- What Is Hacking Tools
- Hack Tools
- Hack Tools Online
- Hacker Tools Software
- Hacking Tools Windows 10
- Hacker Tools
- Hack Website Online Tool
- Hacking Tools Usb
- Pentest Tools Subdomain
- Hacking Tools Windows 10
- Nsa Hack Tools
- Hak5 Tools
- Pentest Tools Website
- Pentest Tools Online
- Pentest Tools Tcp Port Scanner
- Hack Tools
- Hacking Tools For Mac
- Hak5 Tools
- What Are Hacking Tools
- Hack Tools
- Ethical Hacker Tools
sábado, 27 de janeiro de 2024
5 Free Online Courses To Learn Artificial Intelligence
We are living in the era of fourth industrial revolution(4IR), where Artificial intelligence has a significant role to play. This 4IR technology embedded within societies and even into the human body. From Computer enthusiasts to common people, everyone should be aware and learn this breakthrough technology.
We think about gigantic Robots from Transformers when we hear about Artificial Intelligence(AI) which is a fiction in the past but a fact today, capable of transforming the whole tech world. The field of AI consists of more than Robots such as personal assistants, self-driving cars, apprenticeship learning, behavior cloning and so on. To learn about this advanced technology, thanks to the online learning resources which offers great content to get started with artificial intelligence.
Here are the 5 free e-learning courses on Artificial Intelligence
1. UC Berkeley CS188 Intro to AI
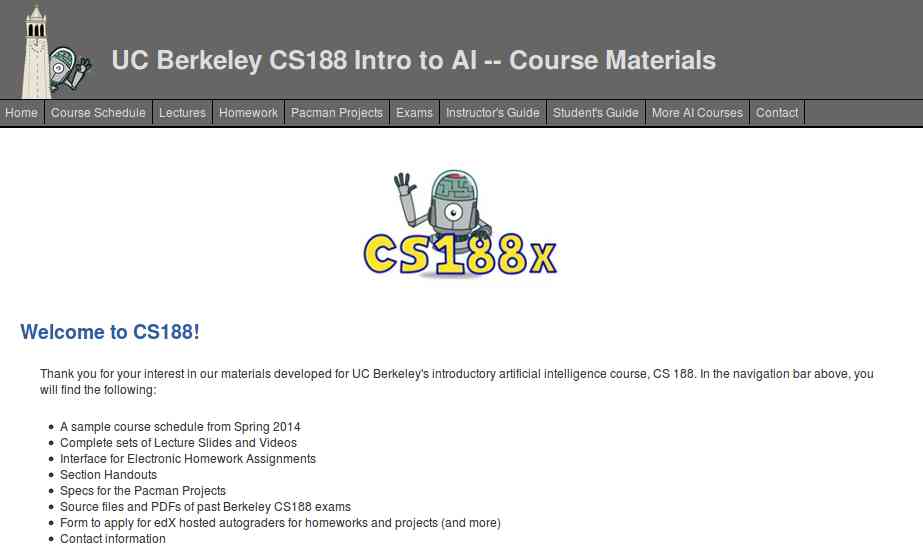
Get started with UC Berkeley AI course, this course is absolutely for beginners who are unaware of Artificial intelligence. It doesn't need any prior computer knowledge to know about AI. UC Berkeley allows anyone to learn this course for free. This course is systematically presented and consists of the following:
- Course Schedule
- Complete sets of Lecture Slides and Videos
- Interface for Electronic Homework Assignments
- Section Handouts
- Specs for the Pacman Projects
- Source files and PDFs of past Berkeley CS188 exams
- Form to apply for edX hosted autograders for homework and projects (and more)
- Contact information
Aside from this, you can also browse the following courses as well from UC Berkeley that are part of AI course:
- Machine Learning: CS189, Stat154
- Intro to Data Science: CS194-16
- Probability: EE126, Stat134
- Optimization: EE127
- Cognitive Modeling: CogSci131
- Machine Learning Theory: CS281A, CS281B
- Vision: CS280
- Robotics: CS287
- Natural Language Processing: CS288
2. Artificial Intelligence: Principles and Techniques
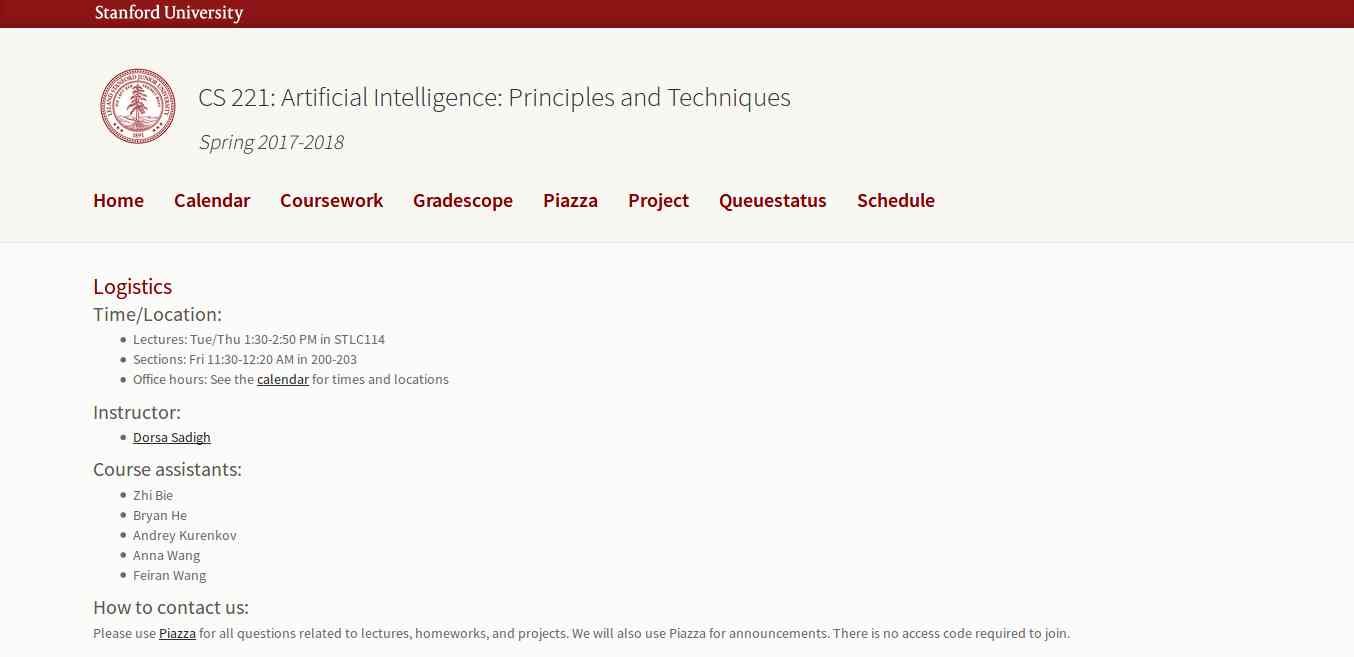
This course is offered by Stanford with great content that includes topics, videos, assignments, projects, and exams. The whole course mainly focuses on the complex real-world problems and try to find similarity between web search, speech recognition, face recognition, machine translation, autonomous driving, and automatic scheduling. Here you will learn the foundational principles of AI and implement some the AI systems. The goal of this course is to help you tackle the real-world situations with the help of AI tools. So, it is the best for the beginner to get started with AI.
3. Learn with GOOGLE AI
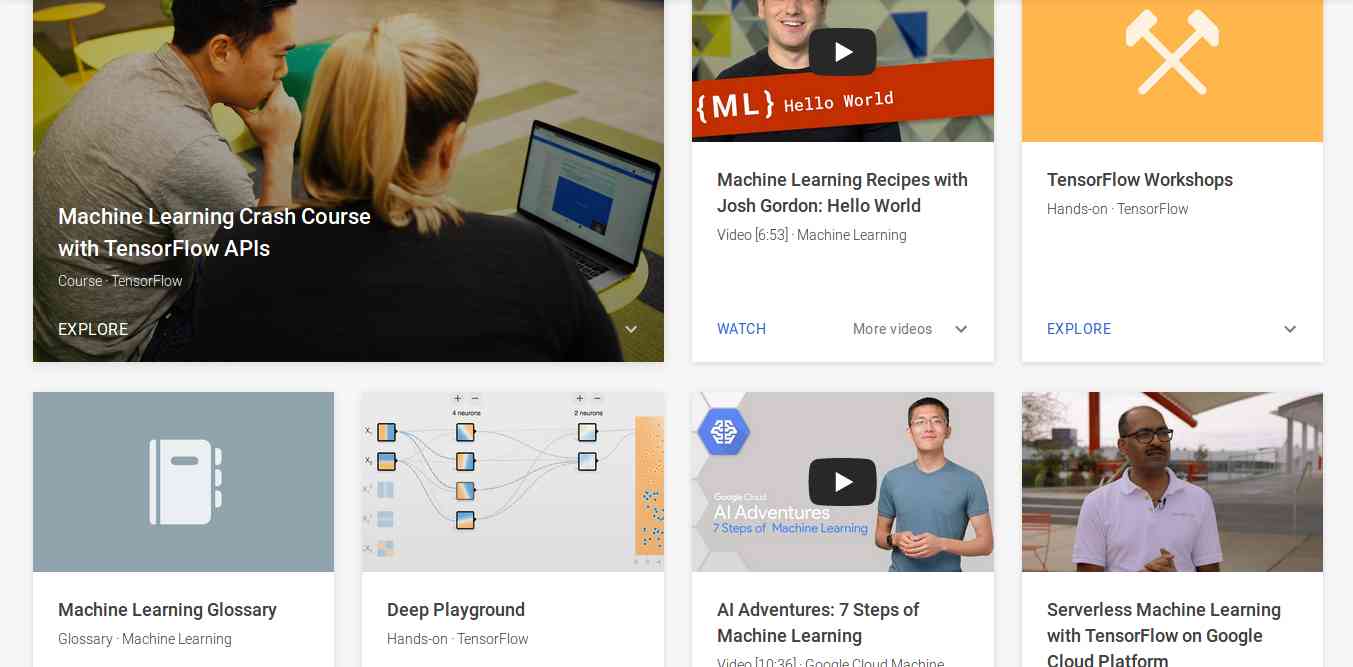
Who will dislike the course from Google? absolutely no one. This company is one of the early adopters of AI has a lot to offer to learners. Learn with Google AI is an education platform for people at all experience levels, it is free to access and browse content. The education resources provided by Google is from the machine learning experts of the company. These resources are the collections of lessons, tutorials, and Hands-on exercises that help you start learning, building, and problem-solving.
4. MIT 6.S094: Deep Learning for Self-Driving Cars
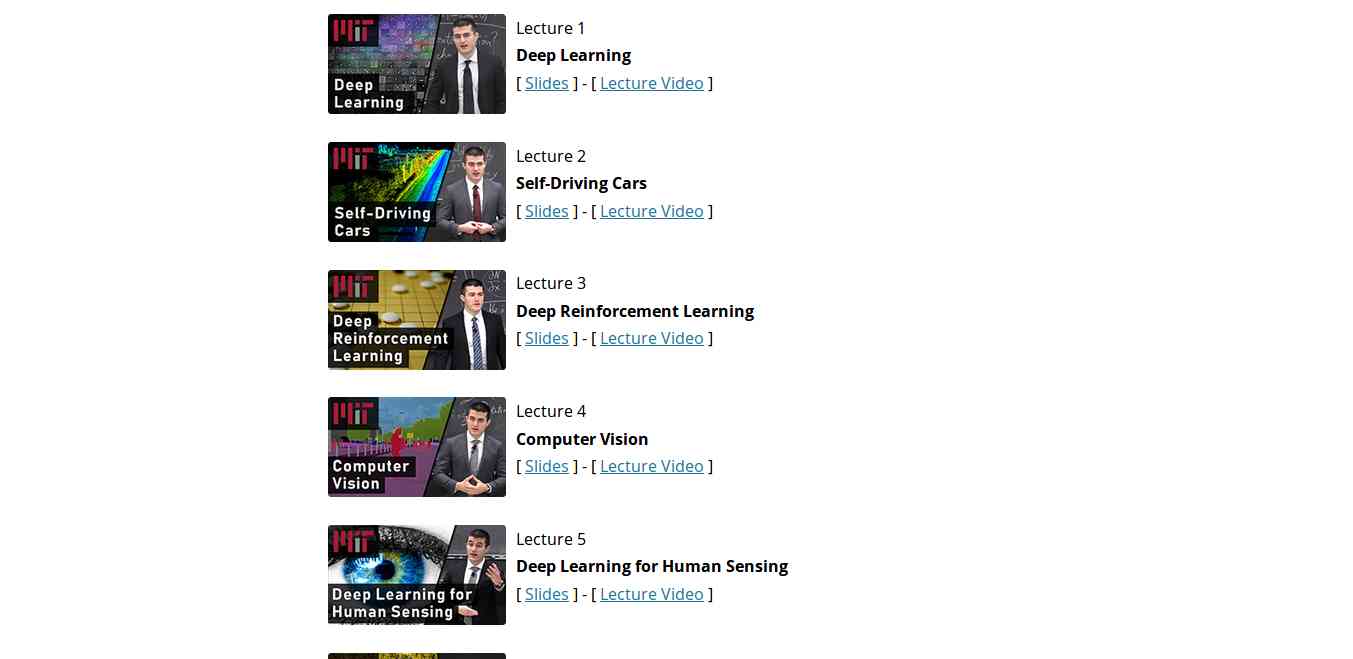
This course gives the practical overview of Deep Learning and AI. It is the course for beginners, also for the people who are getting started with Machine Learning. The course also offers a lot of benefits to the experienced and advanced researchers in the field deep learning. This MIT's course takes people into the journey of Deep Learning with the applied theme of building Self-Driving cars. However, the course also offers slides and videos to engage the learners.
5. Fundamentals of Deep Learning for Computer Vision
This course is offered by Nvidia and Nvidia Deep learning Institute. Computer Vision is one of the disciplines of AI that acquire, analyze, process, and understand images. The course is completely free and everyone who is enthusiast about AI can access and learn the course. It is a hands-on course that able to provide basics of deep learning and deployment of neural networks. With this. you will also learn the following:
- Identify the ingredients required to start a Deep Learning project.
- Train a deep neural network to correctly classify images it has never seen before.
- Deploy deep neural networks into applications.
- Identify techniques for improving the performance of deep learning applications.
- Assess the types of problems that are candidates for deep learning.
- Modify neural networks to change their behavior.
- Hack Tools Pc
- Kik Hack Tools
- Pentest Tools Open Source
- Nsa Hacker Tools
- Hacking Tools Name
- Hacks And Tools
- Hack Tools Github
- Best Hacking Tools 2020
- Pentest Tools For Ubuntu
- Underground Hacker Sites
- Beginner Hacker Tools
- Hack Tool Apk
- Android Hack Tools Github
- Hacking Tools Hardware
- Hacker Tools Hardware
- Hacking Tools For Kali Linux
- Hacker Tools For Pc
- Pentest Tools Bluekeep
- World No 1 Hacker Software
- Pentest Tools For Ubuntu
- Hacker Tools Hardware
- Github Hacking Tools
- Hacker Hardware Tools
- Hacking Tools Name
- Growth Hacker Tools
- Pentest Tools Port Scanner
- Pentest Tools List
- What Is Hacking Tools
- Pentest Tools For Mac
- Hacker Tools 2020
- Pentest Tools Subdomain
- Pentest Reporting Tools
- Hak5 Tools
- Pentest Tools Find Subdomains
- Nsa Hacker Tools
- Best Hacking Tools 2019
- Pentest Tools Nmap
- Hacker Tools Linux
- Hacker Tools Free Download
- Hacking Tools For Mac
- Hacker Tools Github
- Hacking Tools For Windows Free Download
- Hack Rom Tools
- New Hack Tools
- Hacking Tools Online
- Pentest Tools Alternative
- Pentest Tools Github
- Pentest Tools Kali Linux
- Hacking Tools Online
- Hack Tools
- Termux Hacking Tools 2019
- Hacker Tools For Ios
- Pentest Tools Bluekeep
- Hacking Tools Online
- Hackers Toolbox
- Hack Tools Download
- Install Pentest Tools Ubuntu
- Hack Tools Download
- Hacker Tools List
- Hacker Search Tools
- Bluetooth Hacking Tools Kali
- Hacking Tools For Beginners
- Hacking Tools Software
- Wifi Hacker Tools For Windows
- Hacker Tools Github
- How To Install Pentest Tools In Ubuntu
- Install Pentest Tools Ubuntu
- Hacker Tools Mac
- Tools 4 Hack
- Hak5 Tools
- Pentest Tools Online
- Pentest Tools Review
- What Is Hacking Tools
- Pentest Tools Download
- Hacker Tools For Mac
- Pentest Tools Tcp Port Scanner
- Hacking Tools For Pc
- Github Hacking Tools
- Pentest Tools
- Hacker
- Hacking Tools Usb
- Pentest Automation Tools
- Hacker Tools Free Download
- Pentest Tools Android
- Hack Website Online Tool
- Pentest Tools Apk
- Hacking Tools 2019
- Hacking Tools For Windows 7
- Pentest Tools Download
- Pentest Tools Subdomain
- Hacker Tools Windows
- Easy Hack Tools
- Hack Tool Apk
- Tools Used For Hacking
- Top Pentest Tools
- Hacking Tools 2019
- Hacker Techniques Tools And Incident Handling
- Pentest Tools Github
- Hacker Tools 2020
- Hacking Tools And Software
- Hacker Tools Windows
- Hack Tools Online
- Hacker Tools Online
- Tools For Hacker
- Hacker Tools For Ios
- Hacker Tools Linux
- Kik Hack Tools
- Pentest Tools For Ubuntu
- Pentest Tools Linux
- Hack Tools Pc
- Hack Tools Github
- Hacking Tools For Games
- Black Hat Hacker Tools
- Hacking Tools Windows 10
- Hack App
- Hack Tools For Mac
- Pentest Tools Github
- Pentest Tools Tcp Port Scanner
- Hacking Tools For Windows 7
- Hack Tools For Windows
- What Is Hacking Tools
- Hack Tool Apk
- Blackhat Hacker Tools
- Hacking Tools
- Hacker Techniques Tools And Incident Handling
- Pentest Tools For Windows
- Hacking Tools Usb
- Hacker Tools For Ios
- Kik Hack Tools
- Pentest Tools For Windows
- Hackrf Tools
- Pentest Tools For Mac
- Hacking Tools Usb
- Hacking Tools Windows
- Pentest Tools Linux
- Tools For Hacker
- Hacking Tools For Windows
- Pentest Tools
- Hacking Tools For Windows Free Download
- Hacker Tools List
- Hacker Tools Hardware
- Hacker Tools Linux
- Hacking Tools For Kali Linux
- Hacking Tools Free Download
- Hacker Tools For Windows
- Wifi Hacker Tools For Windows
- Pentest Tools For Android
- Hacking Tools Github
- Best Pentesting Tools 2018
- Hack App
- Pentest Tools Open Source
- Github Hacking Tools
- Kik Hack Tools
- Physical Pentest Tools
- Hacking Tools Windows 10
- Pentest Tools Website
- Hacking Apps
- Hack Tools For Windows
- Usb Pentest Tools
- Hacker Tools For Mac
- Pentest Tools For Ubuntu
- Usb Pentest Tools
- Underground Hacker Sites
- Hack Rom Tools
- Pentest Tools Free
- Hacking Tools For Pc
- Hacker Tools For Windows
- Pentest Tools
Assinar:
Comentários (Atom)








